In the current round, the email contains the real name of the executive (we have confirmed it is not only CEOs, so that is also consistent with the previous attacks), and their real telephone number in the body of the email. Here are some excerpts from one such email . . .
SUBPOENA IN A CIVIL CASE
Case Number:
(numbers here)
United States District Court
YOU ARE HEREBY COMMANDED to appear and testify before the Grand Jury of
the United States District Court at the place, date, and time specified
below.
...
Please download the entire document on this matter (follow this link)
and print it for your records.
...
Failure to appear at the time and place indicated may result in a
contempt of court citation. Bring this subpoena with you to the
courtroom and present it to the bailiff.
The initial domain used in the attack, "cacd-uscourts.com" was registered through the Registrar "Web4Africa" on April 12th. On Monday, we had the good fortune that someone reported this phish to the CastleCops PIRT Team, where it was assigned PIRT #792683. Monday evening, PIRT received an email back from Web4Africa informing us that the site had been disabled, which they did by changing their NameServers to "suspended1.web4africa.net" and "suspended2.web4africa.net", as you can see in their Current WHOIS record.
I wasn't able to fetch the malware the first round, as I was away from my lab at the incredible Usenix LEET 08 Workshop, where I was able to meet some security heroes of mine, Thorsten Holz and Neils Provos, the authors of Virtual Honeypots: From Botnet Tracking to Intrusion Detection. (Subliminal mode on -- Buy this Book! -- Subliminal Mode Off).
I got home Wednesday afternoon and went straight to the lab, only to learn that the Phisher was stupid enough to immediately try again. When I arrived in the lab, I checked for other sites hosted by the original nameservers and saw that a new domain name had been registered early Tuesday morning. They chose a different name, "casd-uscourts.com", which they hosted on the exact same IP as the other box, (which incidentally hosts several other malware sites which infect their visitors by installing software via "IFRAME" and Encrypted Javascript techniques).
We used CastleCops to get the site shut down again last night, but not until we first made some screen shots and infected a goat machine with the malware to see what it would do. (Thanks to two of my UAB CIS graduate students for staying late and working on this last night!)
The site is using ActiveX to deliver its malware, and requires an Internet Explorer browser, as you can see from the two screen shots below:

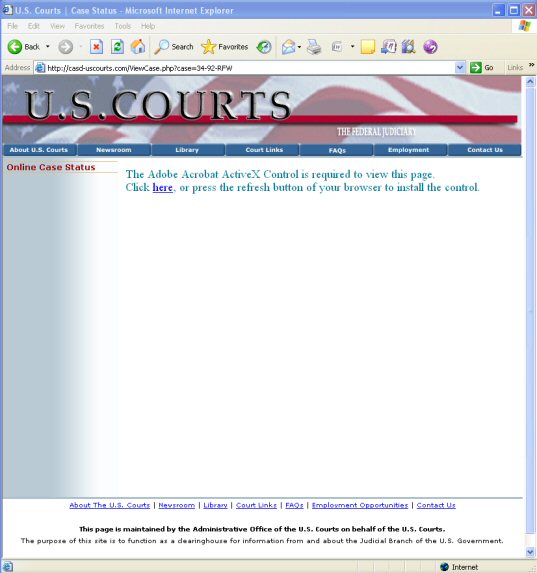
Several people have said "No CEO would click on a subpoena in email!" That's probably true. The CEO would probably send it to the corporate counsel, who would click on the subpoena in email.
Regardless WHO clicks on it, here is what happens if someone does:
The browser goes to "Acrobat.php", which causes the creation of a hidden file called \Windows\system32\Acrobat.dll.
The registry is modified by placing the value: "rundll3d acrobat.dll Anit" in the registry key: \HKLM\Software\Microsoft\Windows\CurrentVersion\Run
A listening port is opened (in our case it was on port 1900).
Every 60 seconds, the machine notifies this computer in China of its infected status by visiting a URL like this:
http://124.94.101.48/MMM/parse.php?mod=cmd&user=MachineName
where MachineName is the system name of the machine in question.
That is probably all the details I'll share for now.
If anyone has observed network traffic going to this IP, there is a very good chance someone in your network is infected. I'd love to know what other communications your infected machine is exhibiting. Please do send me an email!






0 comments:
Post a Comment