While I have some head knowledge about fuzzing - having read and played with the book Fuzzing: Brute Force Vulnerability Discovery,
 what really made me understand its value was working a Penetration Testing engagement with Packet Ninja Daniel Clemens. Dan does most of his work at a hand-crafted "ninja intuition" level, but when he has discovered a potentially vulnerable app, he's absolutely willing to throw a fuzzer at it and let it churn. In this case, I got to watch him in action with Burp Intruder.
what really made me understand its value was working a Penetration Testing engagement with Packet Ninja Daniel Clemens. Dan does most of his work at a hand-crafted "ninja intuition" level, but when he has discovered a potentially vulnerable app, he's absolutely willing to throw a fuzzer at it and let it churn. In this case, I got to watch him in action with Burp Intruder.I knew that Dragos, another famous fuzzer, listed Burp Intruder as one of his Ten Favorite Web Application Fuzzing Tools. But watching this tool in the hands of a master Pen-Tester like Dan really made the lights come on for me!
Still, its one thing to fuzz forms on a website, and quite another to fuzz applications (although Dan does that quite successfully, too). When I heard about Charlie's "three-peat", winning PWN2OWN for the third consecutive year, I started hitting all the blogs looking for first hand accounts from people who were there. One of the most amazing things to me was that Charlie claimed to have found all of these vulnerabilities using "a dumb 5-lines of python fuzzer". I got some hints that things were more complicated than that by looking at some slide-shots from CanSecWest 2010 In Pictures, including scary ones like this:
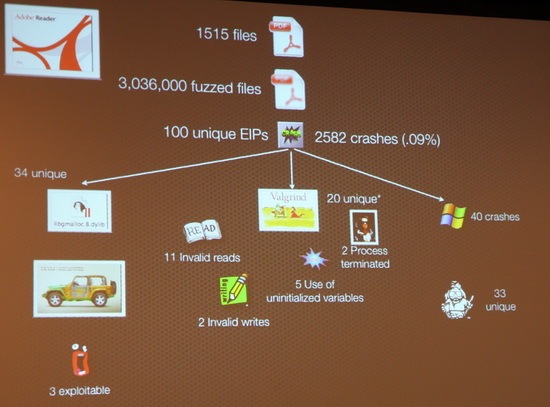
and

(pics from "infosecevents.net")
Charlie's talk demonstrated his results using his fuzzing technique on PDF files using Adobe Acrobat Reader and Mac PDF Preview and on PowerPoint files, using Open Office PPT, Microsoft Office PPT. From his previously discussed work in Safari and IE we know that his techniques have much broader implications.
Today I finally got a much deeper understanding when I saw from the Thoughts from a Technocrat blog that Charlie had posted his CanSecWest slides from his presentation -- Babysitting an army of monkeys: an analysis of fuzzing 4 products with 5 lines of Python (PPT file).
His presentation contains this hint at the Five Lines of Python you've been breathlessly waiting for:
numwrites=random.randrange(math.ceil((float(len(buf)) / FuzzFactor)))+1for j in range(numwrites):rbyte = random.randrange(256)rn = random.randrange(len(buf))buf[rn] = "%c"%(rbyte);
Charlie actually recommends three other presentations on fuzzing within his slidedeck:
Fuzz by Number - Charlie Miller, 2008
!exploitable and Effective Fuzzing Strategies as a Regular Part of Testing - Jason Shirk, 2009
Effective Fuzzing Strategies - David Molnar and Lars Opstad, 2010
If you are responsible for ANY application security, you really need to evaluate Charlie's methods. His setup involved fuzzing for three weeks on five Mac OS boxes. Surely the authors of major web browsers can afford a setup of at least that complexity? Hmmmm....(dear students, what do you think *WE* could set up???)
Charlie's Fuzzing book is available at Amazon.com:

Fuzzing for Software Security Testing and Quality Assurance
Be sure to follow Charlie on Twitter if this is a topic of interest to you:
http://twitter.com/0xcharlie
(Full Disclosure: For the observant, yes, the Amazon links in this presentation are affiliate-tagged. If enough of you buy the books, my copy is free. When I buy security books they go in my library for students in the UAB Computer Forensics Research lab to use. If you want to send us free books some other way, that's cool, too. 8-)






0 comments:
Post a Comment